Is your organization prepared for the increasingly sophisticated and pervasive cyber threats that are challenging enterprise CIOs and IT leaders? Our previous analyst perspective underscored the importance of protecting digital assets and driving business growth with Continuous Threat Exposure Management (CTEM) — a proactive approach to identifying and managing cyber threats. In this perspective, we delve into the crucial business and technology considerations that enterprises must weigh when evaluating CTEM software and providers.
Our market research has identified five key factors that have been instrumental in shaping the most challenging security incidents faced by enterprise organizations.
Firstly, 95% of participants pointed to security detection capabilities as a significant factor. This was closely followed by the security technologies deployed, which was highlighted by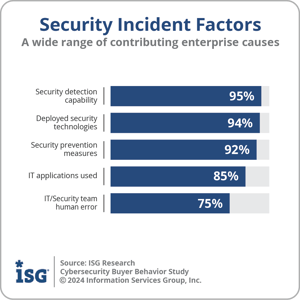 94% of participants. The organization’s security prevention measures were also a major concern, with 92% of participants acknowledging their importance.
94% of participants. The organization’s security prevention measures were also a major concern, with 92% of participants acknowledging their importance.
The IT applications used were identified by 85% of participants as a contributing factor to challenging security incidents. Lastly, 75% of participants cited human error within the IT and security teams as a key element in the occurrence of these incidents.
Our research further reveals that phishing poses the most significant challenge for an enterprise’s security incident management. On the other hand, our research also demonstrates that prior investments in detection tools have paid off as malware and viruses were cited as some of the least challenging incidents for an organization.
These findings suggest a need for a shift in resource allocation. Rather than focusing on detection and remediation of these common security threats, resources should be channeled towards threat hunting and the identification of new threat vectors. For instance, vulnerabilities emerging from the supply chain and partner networks could potentially move laterally into the enterprise, posing a significant risk. Thus, these areas should be prioritized to enhance the overall security posture of the enterprise.
Cybersecurity is not just an IT concern but a crucial business objective. CTEM aligns with this perspective by offering benefits that extend beyond the realm of IT and contribute to overall business goals. Some of these objectives include:
- Risk management: CTEM aids in effective risk management, a key business objective for any enterprise. By providing real-time visibility into threats and automated response capabilities, CTEM reduces the risk of data breaches and the associated financial and reputational costs. For instance, a retail business could use CTEM to protect customer data, thereby preserving customer trust and loyalty.
- Operational efficiency: CTEM can enhance operational efficiency, another important business objective. By consolidating various security functions, CTEM simplifies security operations and reduces the time and resources required for threat management. This could be particularly beneficial for a manufacturing firm, where streamlined operations can lead to significant cost savings.
- Regulatory compliance: In industries subject to strict data protection regulations, such as healthcare or finance, CTEM can assist with regulatory compliance. By continuously monitoring the enterprise’s threat landscape, CTEM ensures that potential compliance issues are identified and addressed promptly. A healthcare provider, for example, could leverage CTEM to safeguard patient data and meet HIPAA requirements.
- Business continuity: CTEM supports business continuity by minimizing the downtime associated with security incidents. Critical business operations can continue uninterrupted, thereby preventing revenue loss. An e-commerce platform, for instance, could use CTEM to maintain site availability, delivering a seamless shopping experience for its customers.
The benefits of real-time threat visibility, improved response capabilities, enhanced security posture and consolidation of security functions help transform the enterprise approach to security threats from a passive activity to one that is proactive and predictive. CTEM software can align with the business objectives of modern enterprises and help them achieve their goals.
To implement CTEM tools in an enterprise, the first step is to understand the existing IT infrastructure. This helps identify the current security protocols, the network architecture and potential points of integration for the CTEM tools. For instance, legacy systems might need to be updated or replaced to work with modern CTEM tools.
After the assessment, the scope of the implementation is defined based on the business needs and objectives. This could involve deciding which departments or processes would benefit most from the CTEM tools or determining the level of threat visibility required. For example, a healthcare provider might prioritize patient data systems for CTEM implementation due to their sensitivity.
In the aftermath of security incidents, IT leaders have been proactive in taking measures to mitigate future risks. Our research has identified five leading actions that occur in response to a challenging security incident.
The most common action, as reported by 50% of participants, is to enhance protection. This is followed by improving technology, which was reported by 33% of participants. A review of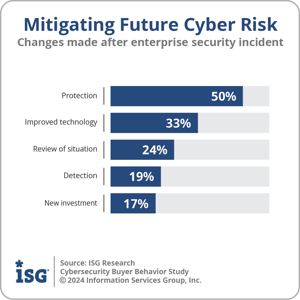 the situation was undertaken by 24% of participants, while better detection and new investments were reported by 19% and 17% of participants, respectively.
the situation was undertaken by 24% of participants, while better detection and new investments were reported by 19% and 17% of participants, respectively.
This data underscores the need for enterprises to adopt an integrated tool that can predict and automate threat detection and response, such as CTEM. The fact that enhancing protection and improving technology are the most common responses to security incidents suggests that enterprises are actively seeking more effective and efficient ways to safeguard their systems.
Moreover, the focus on better detection and making new investments indicates a recognition of the evolving nature of security threats and the need for continuous innovation in response strategies. CTEM aligns with these priorities by providing a comprehensive and proactive approach to security management.
The next step is to integrate CTEM tools with existing technologies. Factors such as compatibility, scalability and potential impact on system performance must be considered. In a manufacturing organization, for example, the CTEM tools would need to work with the industrial control systems (ICS) and not disrupt their operation.
The final step is to train the IT team to use the CTEM tools effectively. This validates that they can utilize CTEM to its fullest potential and respond swiftly to any threats.
When evaluating CTEM software providers, there are several capabilities to look for:
- Real-time threat visibility: This allows for immediate detection and response to potential threats.
- Automated response capabilities: This enables the system to react to threats even when security analysts are not available.
- Comprehensive reporting: This provides insights into the threat landscape and the response strategies.
- Scalability: This ensures that the software can adapt and scale as the enterprise grows and evolves.
When interacting with software providers, it’s important to ask about their support services, the frequency of updates and how their approach adapts to evolving threat landscapes. Consider evaluation options, such as a trial period or demo, to assess the software’s fit within the specific environment.
Cyber threats continue to increase in complexity and sophistication. It’s imperative for CIOs and IT leaders to enhance their organization’s security posture and consider implementing CTEM software. Several business and technology considerations must be balanced in the strategy assessment and software provider evaluation process. Threat detection and response is one of many cybersecurity topics analyzed in our coverage of Digital Security.
In the face of ever-evolving security threats, enterprises need advanced, integrated approaches like CTEM to predict, detect and respond to security incidents effectively and efficiently. This not only aligns with their current requirements but also paves the way for a more secure future. We encourage you to sign up for our Ventana Research community and stay current with security content and analysis from our team of experts.
Regards,
Jeff Orr

 94% of participants. The organization’s security prevention measures were also a major concern, with 92% of participants acknowledging their importance.
94% of participants. The organization’s security prevention measures were also a major concern, with 92% of participants acknowledging their importance. the situation was undertaken by 24% of participants, while better detection and new investments were reported by 19% and 17% of participants, respectively.
the situation was undertaken by 24% of participants, while better detection and new investments were reported by 19% and 17% of participants, respectively.








